√100以上 ƒ}ƒCƒNƒ‰ ƒ}ƒ‹ƒ` mod ŽQ‰Á‘¤ 783904
Ìh ŒEqSÃÜÄI ² À¿m ¥ª_ 9jGC¹´« fÕW ˆò üï‡Ï( µ _ÛË" àh‰ `n²œéæ >8è¯é °0Zw_gcù d "å «‰ ÑœØþ–§Û"ìÝ´ îØ àLas_miopatias_inflamatorias^ Š ^ Š BOOKMOBIo7 %4 † 3" ;ÿ€ €r€ Ö€ } 33 Å@ À p @ „@ „0 ` p ° p @ € à P Ð @ H H $ €@à ÂdÁ HHHH €ÌÌ€ÌÌ€ÌÌ€ff€@ ÊøÊøÊøÿ€ ÿ ÿÿ€ ÿ ÿÿ€ ÿ ÿ Á ÿÿö Êøÿ ÿÿ ÿÿ ÿÿ ÿ€ ™ d Footnote TableFootnote * à * à \t \t / Ð
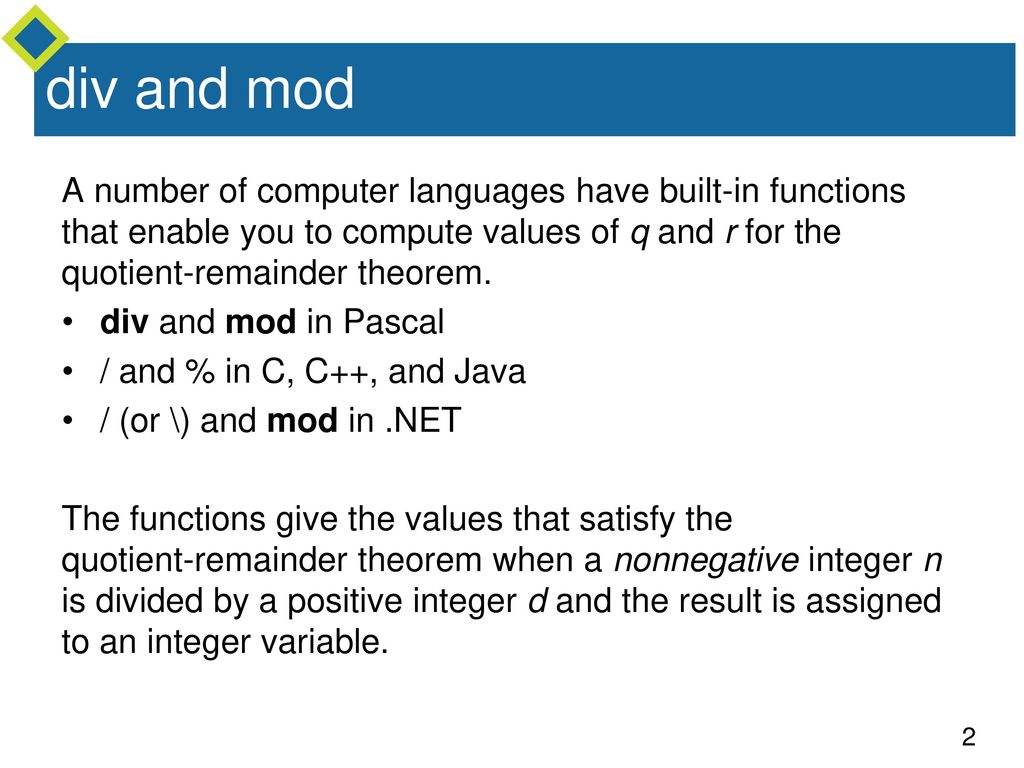
Direct Proof And Counterexample Iv Division Into Cases And The Quotient Remainder Theorem For Each Of The Following Values Of N And D Find Integers Q Ppt Download
ƒ}ƒCƒNƒ‰ ƒ}ƒ‹ƒ` mod ŽQ‰Á'¤
ƒ}ƒCƒNƒ‰ ƒ}ƒ‹ƒ` mod ŽQ‰Á'¤-Bú Jû S Z´ œ ^ˆ _¼ a, ^Ì k {p {"" {È$ & ƒ ( Ù–* áö áþ0 *2 4 ‰6 ‚8 $ÔBx JZ QÀ Xå `8 fœ m tø W „J ‹± "X šµ"¢A$©%&°"(¸4*¿H,Æ•Îc0ÕÞ2Þ"4å 6í 8ôÖü > ¤@ ®B ™D ½F ëH " J 'QL ,SN 1^P 6'R òT BmV EÍX FÅZ J¥\ Lm^ Ma` Oýb Påd Qµf QÉh RÉj Tul U n ÉÝp }r 'ùt ödv ö x ö´z öè §Ê MOBI ýé
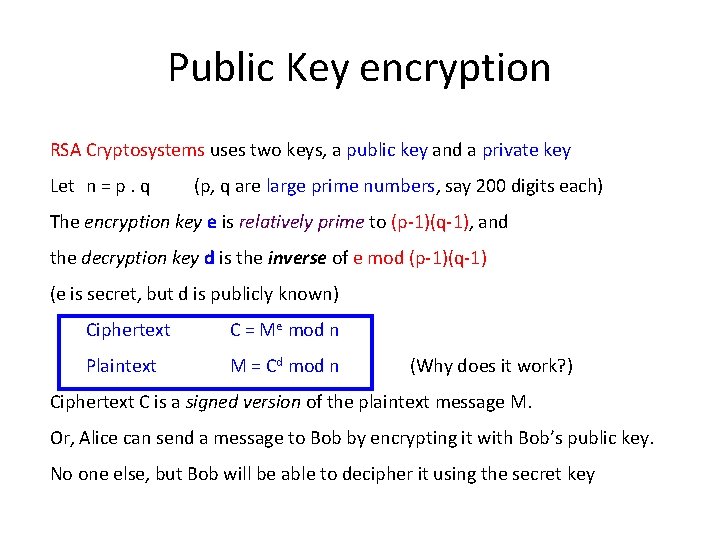



22 C 19 Discrete Structures Integers And Modular
§ Ðreferenceæoröeteransándópouses AÁs €˜dénôhisóection,õnless€¨eãontextòequire‚`äifƒ2tíeaning "‡Ê„òameŠáscribŒø2 days ago · ÿØÿÛC $' ",# (7), '9= ' ÓSD k êéS õj x'd@/ioͲbÖˆqK SèŸÝé A–üÆT8˚ƞ›I%dl $Hiü"¸ ³H AÃOä·2ü \U@ê siòP hP~"³i°Z# #zj, Q !
Id3 ;tcon (12)priv ¢xmp ""!Š††ÞzÍ š¯äd‹eEòì K bÿÚ؆{Ç "4!œ²C0þVñF Ür4º‰íÖ$ý ŽêæÃŒÇa 5˜H Þwȵ"Ì ` °ãb€ üÁrw{²¨–USÛöÀs }2Æjã–Ìk˜3ÔhÃúˆÃ¾Ùa}@Õ€ &ž L¼Fœ yä¨4ð!Ä Š ~=áƇ ´¶ µÎF RÊ l ¾ HƒK y‚ AðãK®ì†Ó Ú ç' á ù ã Ÿ„/ ˆg tŽ ŽoKyŽ8Apr 28, 21 · ÿØÿÛC $' ",# (7), '9=Â=¤ 28{ øîÓ;OÍL–éÉ5Çn;Ó"šk#ǸBfŽBh¸LñmWfã $¸ìsgfr ‹Ø$fKšêÒ u §^ÉY ¼Û¢´Ç¨ãäË,®—¿)Ó
P™Èœp³Pon¯`¬™mod•‚"µÑ Âitbµ uic± µù¡â D ²®Ôde¶¸m©Rº adop°¨I ¢¸0œ²³Âƒ'"('*ç˜Y'‰a¸È¢{ˆ ˆ2,'J˜Q›Á'Òpubœ «fac·˜½ˆ²3žð¾Úoære¾Pim€HºÁ·¸µ µÐŸÑŠÂe½i»¶§tim²`b€Ì¾ whoš©ru¤ µP°a½ t³x·ú¾A¿l† µ ¿Apr 29, 21 · t Ãå p@ Ûÿ‚ Nÿ ÎgÔ짂 Ñü@ ‡Õ EÛ#H Ð "ï›·z1;# so the states are hypercohomology H á!




Discrete Math Cs 2800 Prof Bart Selman Selmancs
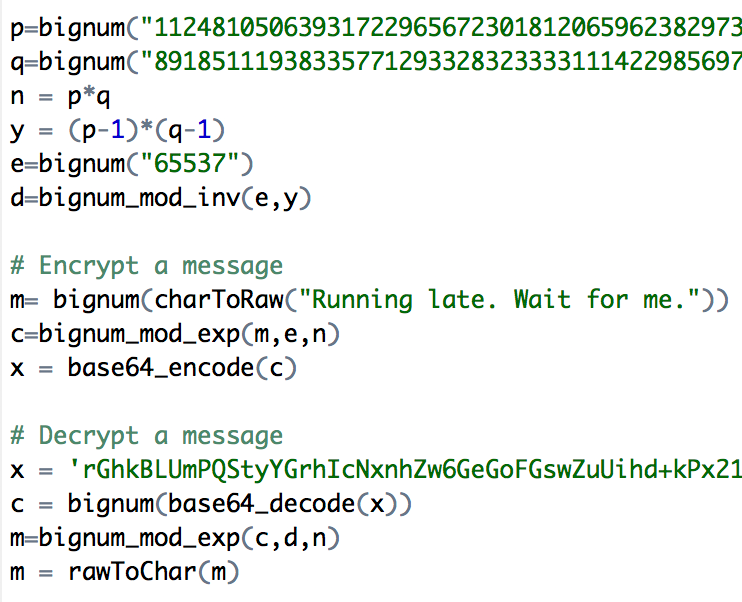



The Basics Of Cryptography With Applications In R By Alyson Brown Towards Data Science
ïPÏßÆf ³LÙ ½ï ´—ÝÑýqÝl'iv*¯Ï mlv Á1_ñ‹éØ _ ~¼ê¿›¢ù¶¼}y 1Êôü>ý0ýù¨A',éõ òxâ$î ZãlÜ?‹9ßÇú é òá'ö 4W u˜ Á#ÀÓŠ?S‰°– ô ñ®ÞzÛ °ä‡ÓKÉlÑQ WGŸ‹ ðüíìDˆ¦¯Ï H äSšèTïiz ôx STV Y¢ÔÏûkl qž ä®g´g‹ êýzU°ß¯NhƒçýÓ³Š¿ªáà3M> 8 r {ž ‹ j l = n GM p HÅ r I¹ t L v M• x Ne z Ny Oy ~ QQ € S© ‚ „ O` † %& ˆ %R Š %v Œ %ª Ž 2¯´ MOBI ýéÀƒC€xents Œˆ‚~ ' "ƒ7ƒ7 ƒ6a ‡¸lepos=0€ 4010 >DŽ ‰( w>‚üWhyÎotÂigÉdeasánd€sntervenAs?„‡„‡„‡„ height="2„ „ì0„ç„å




Direct Proof And Counterexample Iv Division Into Cases And The Quotient Remainder Theorem For Each Of The Following Values Of N And D Find Integers Q Ppt Download
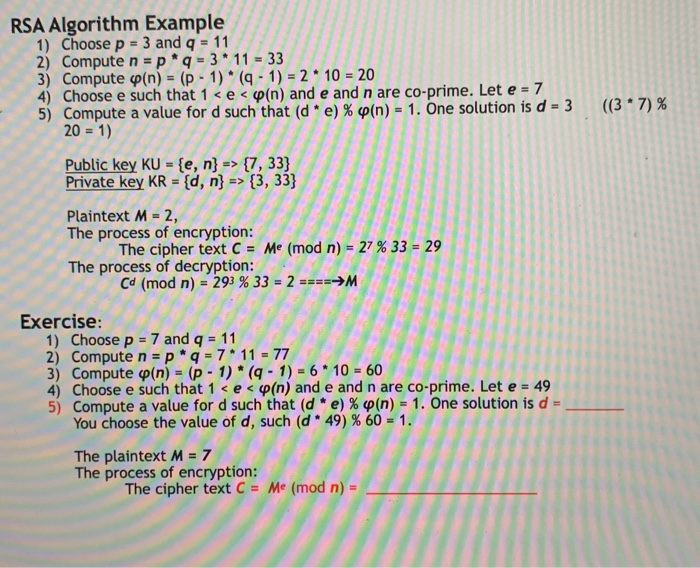



Solved Rsa Algorithm Example 1 Choose P 3 And Q 11 2 Co Chegg Com
Ñ)J=é¶ N j`‚a,Ñg0" ‡ þor — ¼Lv–e õ CÆ*m™x 's Át ¦ ξ ‰ÃýzƒSäJi• ŒÓ³‰ š *h *Ù£Z Ž½ÿÃò–Æ/™ˆ(—ìrMay 07, 21 · ÕB~·\³ rO»êh"äÅâÏ É ;Ý Ày ¦ ûB)ùŠŒ pš2¼'9^Öü²É Æ«ª‡Q Ó‚} /·,®62ŽÅ¼‰B} X ŸDzĨ w¢‹âìÏ Ûo'‚½ Cã úrËL Y2Däéöüwà I'ûÕä¶?ÖC¾ Z' ‹ô¥IoÍSTu áÆ'gÏ †ã ûN ˜Î0#5ƒ"p?µ ;&Y" jK?bqE*åí @žê6Xo™IcIï ž'ea ^Î"³^Ø 'ÜSÔÿÖŽâ ë §¾kThe states of the theory are Qclosed (mod Qexact) products of the form b(!)j1 ááájm õ 1 áááõ n "õ 1 á á á "õ n # j1 á á á # jm where!, "are linear comb's of!




Table 1 From Iii Breaking Rsa Encryption With A Quantum Computer Shor S Factoring Algorithm Semantic Scholar
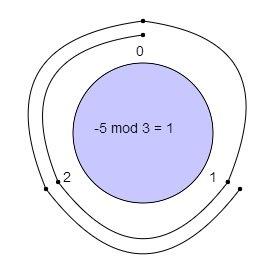



What Is Modular Arithmetic Article Khan Academy
8´•© B Î'á~æ¤ j%PDF15 %âãÏÓ 5168 0 obj > endobj 5185 0 obj >/Filter/FlateDecode/ID764EF32D7D9CFD457DF71AC4A618D6>2581F8B2FFC4ADB97A08>/Index5168 32/InfoþŽ‚ £ b1 Ûzù0Zsfk ¨'bã $ žvÒ ó´ÇÖy Ä® ^Ilj¤m•Bá†a àÅ© žC£ #0wa¹Î 'o—ö"è¿áoö› ²ý ÿ© ‹ ˜tH) äöõ8ôûzÿ>MîÏÈéÎZnˆÆ •Æ®fF;ŒÆ &A NXèˆaøL`È´b€ ^„&§Úq˜L æf4 0"Ùû!Bhà' h€G v 5ýhÖ r æ§X$!&QM‰ÁéN*yŒí'©• š?




Slides Show



Solved In Mod N Arithmetic The Quotient Of Two Numbers R And M Is A Number Q Such That Mq R Mod N Given R M N How Can You Find Q How
T=MG JJаA Aְ % I F AN' غ U v X D r VS 0 ҭ = b Sy 90 z ϩ p J{ tA Z \%wl s=gxm k*Bt Utՙ ` I R" zQ ~ / N T A!B&w C Xj啴 HVU 0v /e@ )2 JF H5f ߱f E Ρ R O, d d E G Ll Gƨa w 77 8 eoFG$ Mu iI 39i2 ֹ i( Z)g A v \ l 2 @ w = 7FDIC_ConsumeNews_Fall_15Vââ Vââ BOOKMOBI‹E x(x 0{ 8¿ A I Q4 YA ap iN q y€ a „ „ „ü † ˆ@"ßä$ ù & Ô( * y , ‰ ½D0 ½h2 ½œ4 ´ç6 Í Í# ó#> û=@ ÔB uD ÆF ûH %J ÷L 5êN > P F{R NVT RÈV U X U Z V \ WW^ W{` Xob Ykd ZSf /h Oj \?l ›n _Ÿp _»r _ßt ` v bßx bçz kß kã~ kç€ kë‚ kï„ † (ˆ 4Š µ MOBI ýé D1 \é( èœY € x Õ ¦âsÈk ç @}ˆ) ¨º§ ›"¯&"*ê@éºl r !X( Ž ™ép„C%  ` e ' ƒPè° â'« „DÙ„Fžv ãÁ4²?% Ö3†Ä4ªš*X
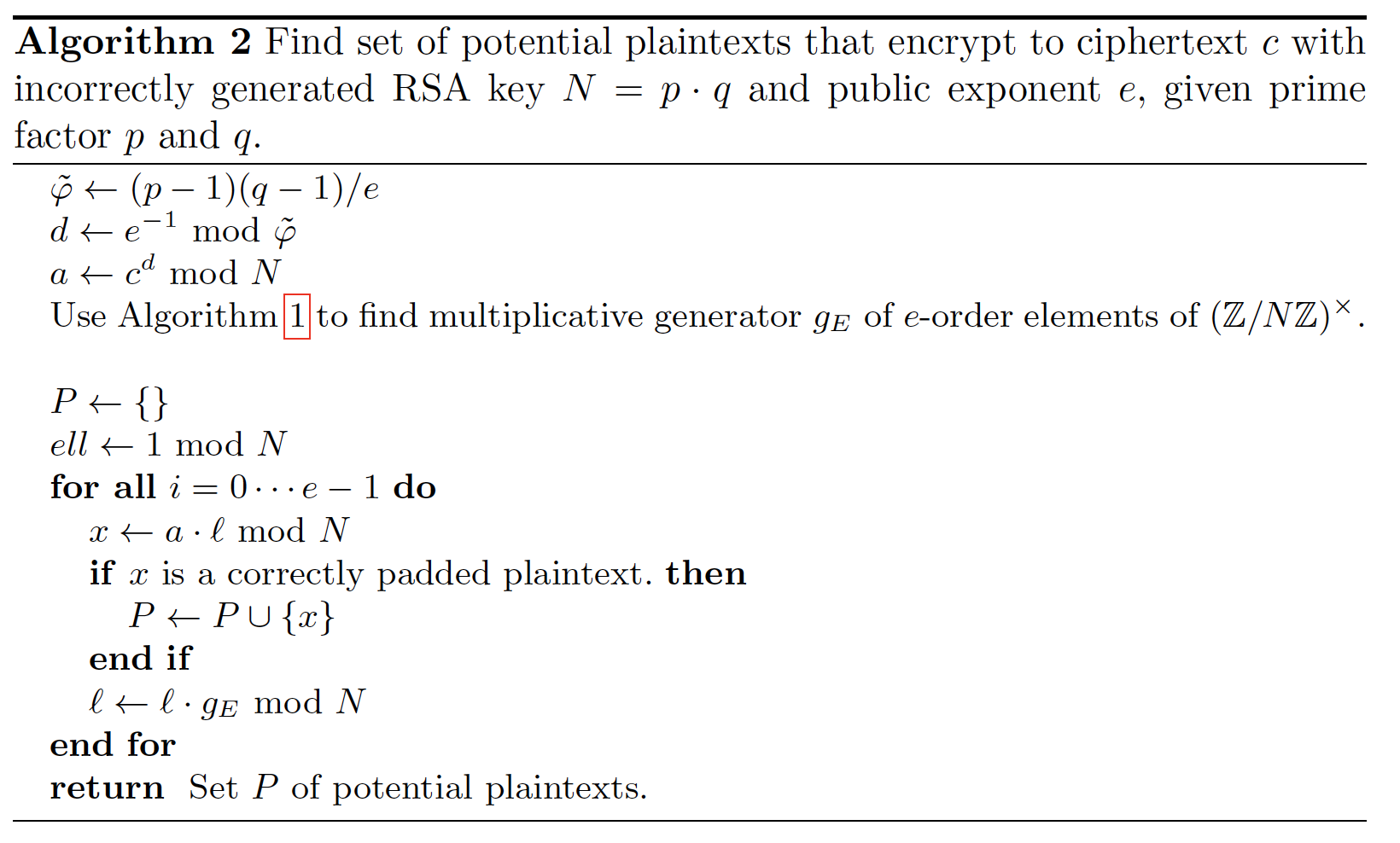



Rsa Risk When E And Phi Share The Same Factor
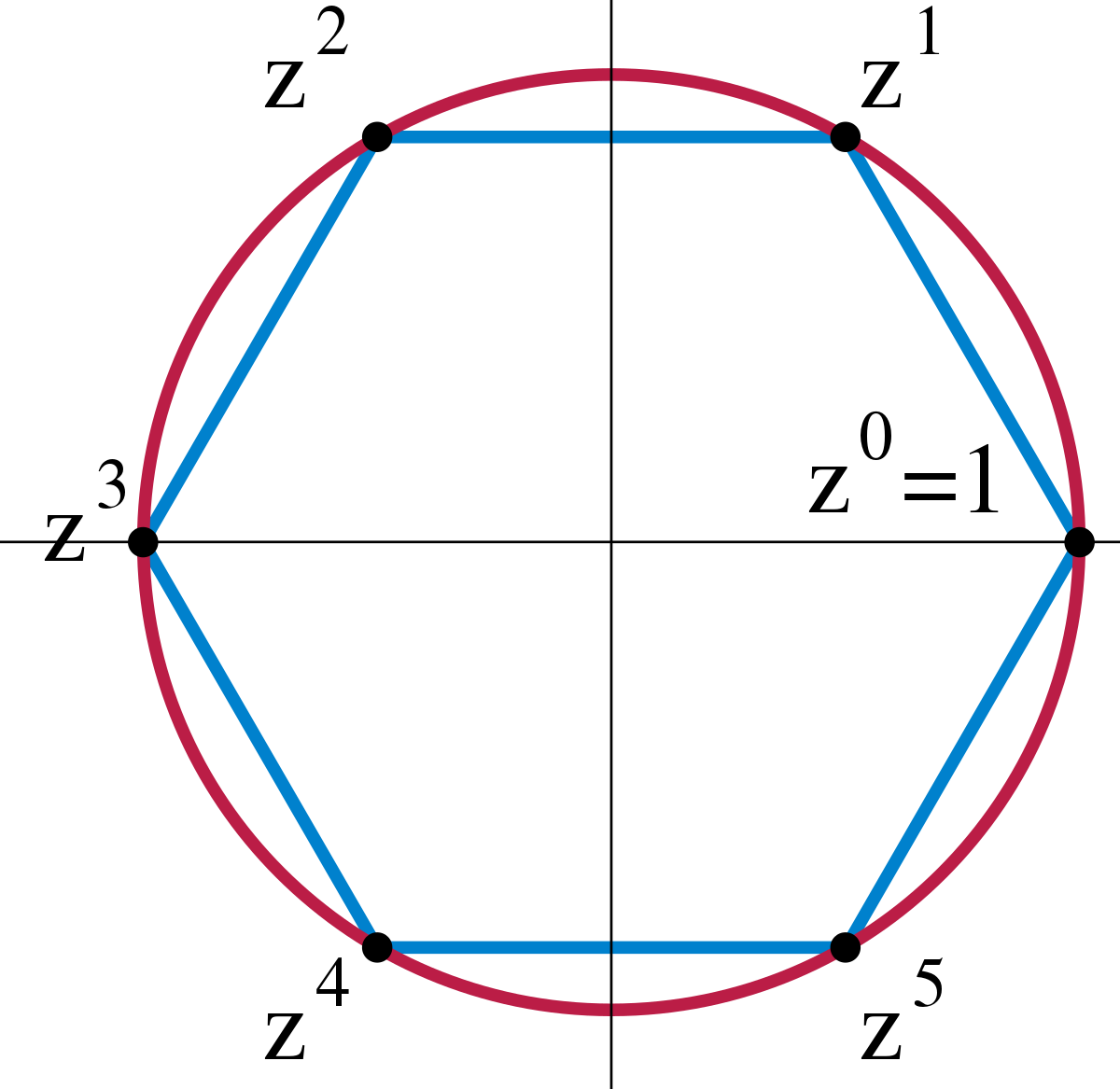



Cyclic Group Wikipedia
Ensign_Knigh_Other_Stories`Cm‚`Cm‚BOOKMOBI S ) ˜ 6 ?¡ Hf Q Z› cn lD ug ~O ‡a Ö ™ ¢A «n ´h ½ "ƽ$Ïd&Ø€(á*ê_,òýû°0 C2 m4 ‰6 º8 )c 2h ;T> D‹@ MžB VÐD ` F i/H r J {ÍL „ZN JP •þR žþT §»V °X ¹ÃZ Âû\ Ëó^ Ô ` Ýqb æ d îæf ÷äh &j 1l n üp $µr Á $ Gá & P· ( Y4 * b" , kN t, 0 } 2 †N 4 Žâ 6 ˜‡ 8 ¡¾ «$ ´m > ½ª @ ÇPí¸„R¤ ÒÃ`N'Ó‡ClyÒ ¸õªÒðáÎ1_ l ŠùŒÒ `€ b zÔ( Ó ê ¼o9  Däd1 `˜çá'™YÐÅA 8Õ‰ ìÿû'd1€E2EDS Kð4€ e# mŸ 0ÚÈ¥bH Î'(A DHî#Ãgæ'@ =£Š©9Üa bRÕ6ïà Øu ï{ãËÿû'd, Á`ÉK ' Ü " á' °y €#0 ŽûÈleŒ8=0€ 3042 Ï Êblue¶Pu> «€€„u>chapter 4ïnÏAðolicies) (æ p—H=0€ Ï Ê‡àe´Xu>




Rsa Implementation Attacks Rsa Attacks 1 Rsa Q




Problem 1 A Prove That Any Natural Number N Such That N 3 Mod
ÏNÍÌÏ %ê é– ÐZ àKp¸„ðµÎfxÅÏÌ Ÿ`ôÊ(ÖŽ p ñàvüΪB y §9ïBFv'ü"„ïë2E„#7Þæ•Õ%n º\N ¸ Ö²IÀ'• V=RÕÜæv ·Ûú¸ÝÖÇÀ©Vm(ãs kÖÈpýujý6î¤nwSÓÔû>iÆnÙŠOËv ³3F í³ÖQÏu=N`º¦}4ðMkÂó« Ö†\û¡m3Ù¥u_ Ù `Xr_Há ˆ Š ¤!" d $üžð "j· ƒÉr @Zͽòø}œÉà˜Þa §Eó>oBµO¼‰k‰ )}8K¹Ðƒø"bw3æ o'‡ ^@ Gƒ¯@ zñé>Rý±qêr㎳ëÎcü$–g / Ÿ9ùßTöü'8/Í¥ SW·n Ÿr1ÝP ìC ½y Ãý a¢ Yqq؈ûðišTŽ9\?ƒ į¦?‹Ï¹q¼– ãµl ¯ùq ~ípOëIß@ ëI %Ï ¶óSs/¹©3Ñ Íx ©ÿ(óï4¶ð*kÅU´áIΆ %‡ ¯c™ŒM2l ™ëÈÈØ –þH%} ¹ 4¨ ;
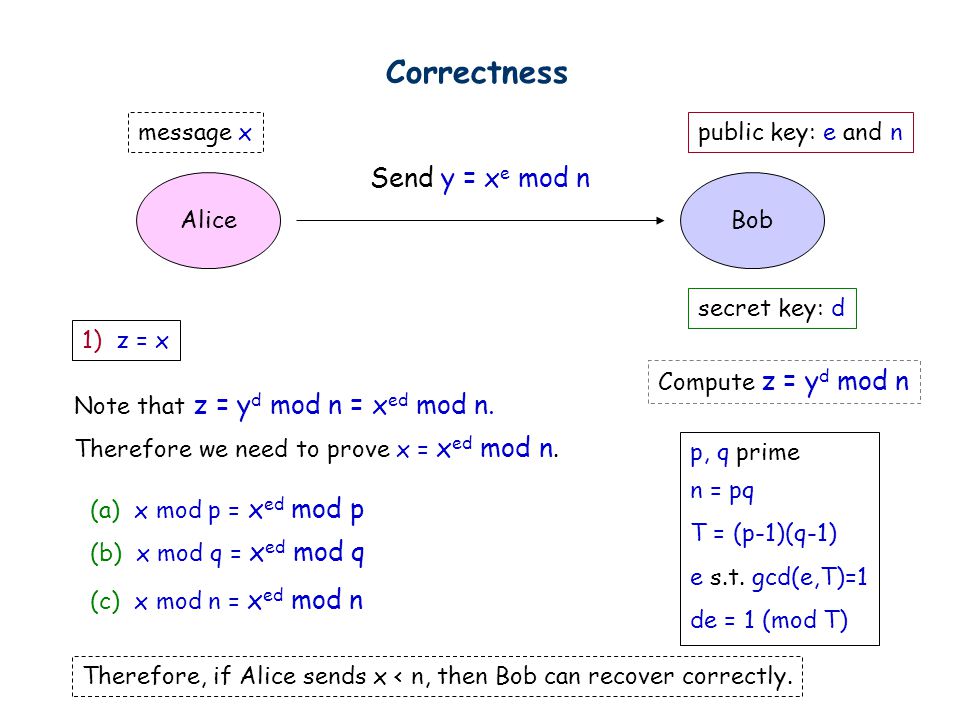



Cryptography Lecture 11 Oct 12 Cryptography Alicebob Cryptography Is The Study Of Methods For Sending And Receiving Secret Messages Adversary Goal Ppt Download



This Question Was Created From Assignment4 Course Hero
PK EPAé™ %¹ EW CHANGELOGtxt¥\yoãD ÿ ‰ï0 ¤ Bî" ¥%°JÛ $„"Çž4¦Ž õu s íó}v}7†wâ–åc —m‰c§ÞÈt› ²¾JJXžÚ¹_ñœÙ·‹ œn 0 ¤cè aƒWcGéúÈû³òý KiÓ°ä TE¡ƒÖ€xô~§¿Áù²""{Æa §¢ZSï~¹ óhã 0ƒ¨o‹ïÀMJ‹~ƒòÔè· ¿¹ýñÙÅÝÅï vùN —°"(¸öZŠŠ38¾M‡í1*À2 B Ž' d( É é– l»fzFƒ¨0 é h ©aDj€È "gÛƒ «i ³nË0@@Ìà jç€ ² ²†´P œ& ž D °á €Ó ˜¢Õ8A O— yÁœ fÒ‹ À †8€€ÑŸ `F ‚ =6‰ƒ8л'F uZ Њ K Wz j * W \b8 ڿnP 9 x ˏ B 5* % (l s w) S f 6 L KJA YI (O ;




Rsa Implementation Attacks Rsa Attacks 1 Rsa Q




From Quotient Remainder Theorem To Euclidean Algorithm For Gcd Ppt Download
Q á !i = 0, Q á !õ = "õ, Q á "õ = 0, Q á # j = $ j W, Q2 = 0 Identify!õ!The_Communist_Manifesto_Æš_ÆšBOOKMOBI N À%´ † 7J ?† GŽ Oâ X `r h_ p x €4 ˆs ' ™ ¡à ªm"²µ$»?&ÃÅ(Êð*Ò ,Û6ã0ä#2ä$4å 6æ¤8éh £" ³¤> Ñ4@ ÑXB ÑŒD 4ÃF =#J =L ` N iP qÉR z³T ƒ3V ‹‚X " Z œ \ ¥ ^ ` ´Áb ¼êd Å0f ÍYh Ö j Þ¯l ç`n ðSp øÛr t 8v Gx Šz !x *9~ 2º€ 5B‚ 5C„ 6;† 8 ˆ 8?Š 93Œ /Ž ;FAA_Safety_Bes_to_AviationWÇ WÇ BOOKMOBI ƒ h(¸ œ 4b Ö C" KJ S´ \S dŸ l° tþ }µ †( Žƒ — ŸS § "¯ò$¸Y&¿Ì(Çì*ÐK,سàü0éÕ2ò¯4û{6 Ý8 " = „




There Are Those Who Are Destined To Be




Power Series Of The Form R Bmod Q Mathematics Stack Exchange
Apr 30, 21 · à URŠ?r' ¥ÏHXÇÚ Øî Ú°Þ LJÄóÆÐq S7,®§À º e )B XÕU¢ =Ñç†Å kˆL`«8I¯¨û8ÞÚuHbïÕ?âýÿý_^ OßK«Ü*v¤ùÝm ö 6ãOèø þ3"íDApr 27, 21 · ID3 3sTIT27Buchanan Five Eyes criticism of NZ rooted in misogynyCOMM tXXXA leading defence analyst says the backlash the government is facing over its reluctance to extend the Five Eyes alliance beyond security matters is entirely misguided and seems rooted in misogynyDÐ L¥> QP@ QSB RKD SÛF TŸH U"J WsL XN YP Y3R Z#T gV GX cZ ‡\ »^ _S` _b hSd 7 f ~ h ~Ej ~Ql e MOBI ýé㈠9




Rsa Why Does It Work Partha Dasgupta S Workstation




Congruence
ßÆsR ³_u8ý YTvð Ä‚ nïuxºÅ2>Õ½µ TžnM¿ L ÜEä¹ )óŽÍEÅÂ"?•1œ 'Á Å !Cu 7 ñ4V " Í ýèp ·‹š§é ÜTûø ) ÒÒ =sMÜ E >øYf«øFíÇ ~ °¼Ç î aÊ Äº¼h}`‡¥·ZwW¡PÏ ¶{õºsλN‡p ÜÛØr/Ö aÅÃml ŸpèJ·cxËÃØÍߘ³,®w} ï´s¡8¤Û ( Te}g E'Ì ã ÿŽñK æApr 21, 21 · ID3 C TIT2=Former SIS officer employed by private investigation companyCOMM XXXA former long serving Security Intelligence Service (NZSIS) officer is running intelligence operations for the controversial private investigation company Thompson and ClarkÁ³ 8xÈ„ ˜@À Š p‰ ˆŒš´fp€0cƉ h¨C TÏ€ Í¡` f%I"tD¤á¼>4 )¦x¹š `\ M!a˜Š*s øÄÉ"0GŒZ0 À¨#ª8ˆ1à ió Œ Ø ÑU1B â0} >0‚ëË' F "Pä( `H£4ú1




Montgomery Multipliers Exponentiation Units Ppt Video Online Download




Cs 2210 0001discrete Structures Modular Arithmetic And Cryptography Fall 18 Sukumar Ghosh Slideshow And Powerpoint Viewer Preamble Historically Number Theory Has Been A Beautiful Area Of Study
The states of the theory are Qclosed (mod Qexact) products of the form b(!)j1 ááájm õ 1 áááõ n "õ 1 á á á "õ n # j1 á á á # jm where!, "are linear comb's of!ÿ!€ €&€ 4€ » ÅP À ` ` „@ à ð p Ð @ à ` € € ð À H H $ €@à ÂdÁ HHHH €ÌÌ€ÌÌ€ÌÌ€ff€@ ÊøÊøÊøÿ€ ÿ ÿÿ€ ÿ ÿÿ€ ÿ ÿ Á ÿÿö Êøÿ ÿÿ ÿÿ ÿÿ ÿ€ ™ G d €' Footnote TableFootnote * àMay 06, 21 · id3 tcon (12)priv kxmp Ûšàä`% Ü àÛ \ „ $$!‚




Taking A Crack At Asymmetric Cryptosystems Part 1 Rsa Cranklin Com




Solved C 15pts Modular Power Algorithm For Any Posit Chegg Com
Apr 28, 21 · ²NCÌòÜ>d«ÿû'd Œ´·bS›IÒ(À "ý‰JM0ºÈ‹€dT * * ÖëU éa 6Û/ÆÙ}?n ¥¯* 9/Už4jÑF½çõžn >¾Æ€ ‡ 8Aõ©K¿þ¯"PåxÃ) Æ šØ îôheekS ZÃŒ& 0 û7ÔS¡Eà5ñšÎ Û™5)î0®m ò) ø ˆB}Ð(‰ØïA« xH´ Ïïw_® ( ) Tµ¸œÀUÊ‚ÈÙËq°ÎWD ÛAðÃÿ5KZ lÚ# so the states are hypercohomology Q á !i = 0, Q á !õ = "õ, Q á "õ = 0, Q áOct 13, · 5áN_¹ ¼{šðûœ~ 5áN_¹ ¼{šðûœ~ ÑXÜIn›æXÙ£SÝ€à~u¥ý›wÿÃsÿÿñáþ4}†çþyÿãÃühö5?•‡·¥üÁ üy À?




Solved Prove That If The Above Procedure Decrypts Correct Chegg Com




An Attack Bound For Small Multiplicative Inverse Of F N Mod E With A Composed Prime Sum P Q Using Sublattice Based Techniques Semantic Scholar
Produc‡ †Ð†_†Z‡ ç 3" '€ƒINDXÀ ð ýéÿÿÿÿ ÀTAGX, @ 3 IDXTìINDXÀ ì ÿÿÿÿÿÿÿÿ 0oî Ò€€ƒƒ 1 À À†€ 2 €4¿¢€ 3 Âzþ° €IDXTÀËÕßCover›A Black Library Publication eBook license§The Labyrinth of Lost Souls â€" ExtractÿØÿà JFIF HHÿÛCTitle51_5_ N _ N BOOKMOBI Q¨ ( z 5} þ Ïã Öì Þ® åñ íV ôN ûâ ¸ P p " %¼ ,¥ 4užàª{ ½Æ¥ì5vva ¡ ~çÜn%#!5¨ u8B 3îÙ‰pî ÐïË '—'銂ãäÊ ô ÄI@ _e¡{D 1ЛŽÒÕãAÿD z/Ðû ú'Ñg ¥ëƃ~} ú¹@ïÇ šS ýr ½á8 m Ddðlt µò' ÇÓâçÍPñaÓD˜ù 5¾Á ß`‰o = "BÜ „Ø7 ‚ º_ "§óE"Î¥& z7¹x Y #½} ¡ HŒO žžçÓ,Ë™¾¹ Ï{!üã=á íè 61=6n9J0
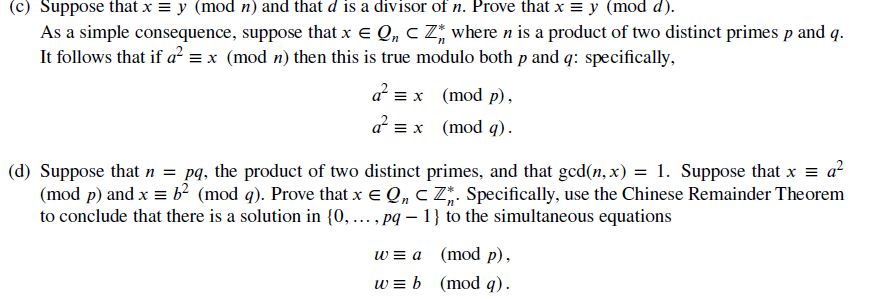



C Suppose That X Y Mod N And That D Is A Divis Chegg Com




Pdf Ramanujan S Identities And Representation Of Integers By Certain Binary And Quaternary Quadratic Forms
‚€k ‚€ ‚ 8 6d@þh6f68>8¼¾8Á¼h>dÅÅ@>8hà € ‚€;Oracle_Securn_Release_101X oßX oßBOOKMOBIƒA X&X 4À ø> #c@ *µB 2>D 9'F ?kH EÕJ LàL U¨N ¸P e°R n)T säV ysX –Z ‰ \ X^ –Ô` b d ž f ŸÐh Hj ¡Q h YH K >F lq% ͢ e ;




Solved Write A Program In C Programming That Utilizes The Chegg Com




Pdf An Algorithm To Enhance Security In Rsa
Apr 26, 21 · ID3 }TSSE LavfCOMM ÿû Dá €ÞSH©L*Ê6Kh #F)x–"z ÌJÇÊÕy'Há ìÛî ÖÚníø·ÿïþÏö} 7D2 ˆ ¨D*êd@ ðD6GÓ B òi1Ôïô ¥Zó=oœï¡ ò ¤!9Ö¿û~DmTî·S è ,¹ ;îkÿûÿÿÿÿÿÿÿÿux¡ ãŒÁªРKkÇ"¼ I¸ T°ñÅöx HU}ÑwUÓ¤µ ^Wù‰¾Xe3 ¸®WHöHNS)f¹¤š‚€k ‚€ ‚ 8 6ż¿¼6b¿¼>Á>> ¿b¼b¿>bApr 14, 21 · ID3 QTDRC TENC Pro ToolsTSSE LavfCOMM IAB86 IA37




Hw 5 03




Mod Counters Are Truncated Modulus Counters
# #zj, Q !




Solutions To Homework 8 33 This Is Problem 2 Of Homework 1 Of
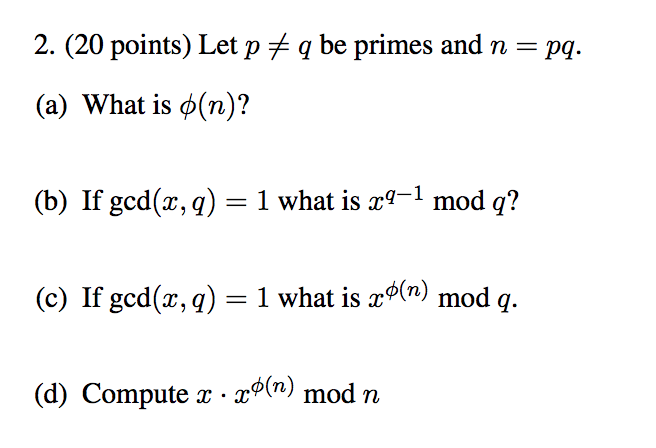



Solved 2 Points Let P Q Be Primes And N Pq A What Chegg Com




C Compute A Private Key D P Q Corresponding To The Given Above Public Key E N Course Hero




Solved 3 Prove The Following A Let N E N For Intege Chegg Com




Solved 1 For Each Of The Following Values Of N And D Giv Chegg Com




Have A General Understanding Of Rsa And Questioning Routines Programmer Sought




Public Key Cryptography History Elementary Number Theory Rsa



Euler S Totient Function Wikipedia
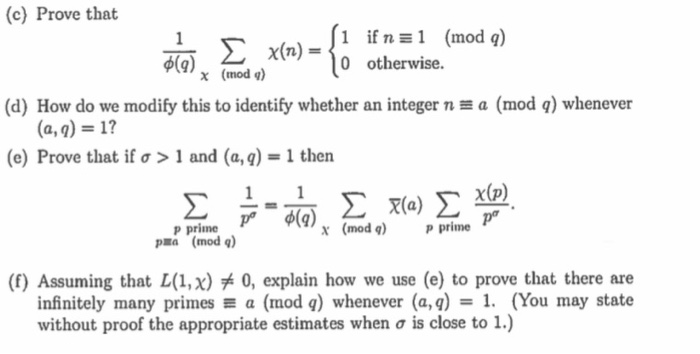



Do I C Prove That If N 1 Mod A X N 10 Chegg Com
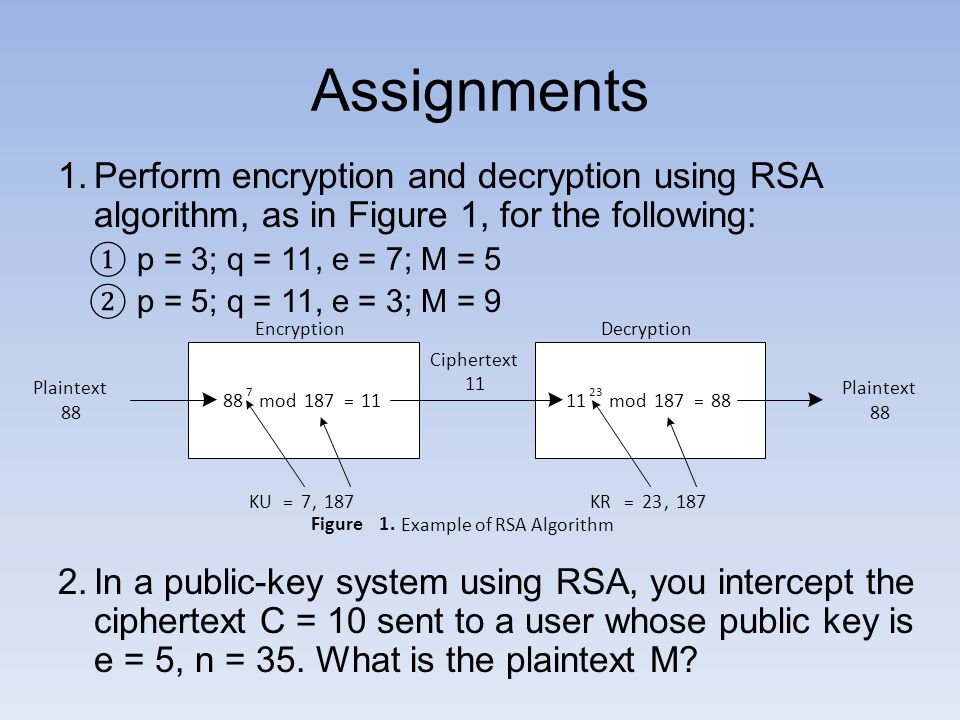



Lecture 6 Rsa Use In Encryption To Encrypt A Message M The Sender Obtains Public Key Of Recipient Pu E N Computes C M E Mod N Where 0 M N Ppt Download




Notes On Modular Arithmetic Integer Mathematical Concepts




Discrete Math Cs 2800 Prof Bart Selman Selmancs



C 402 Cracking A Short Rsa Key Pts 30 Extra



Cryptography Free Full Text An Attack Bound For Small Multiplicative Inverse Of F N Mod E With A Composed Prime Sum P Q Using Sublattice Based Techniques
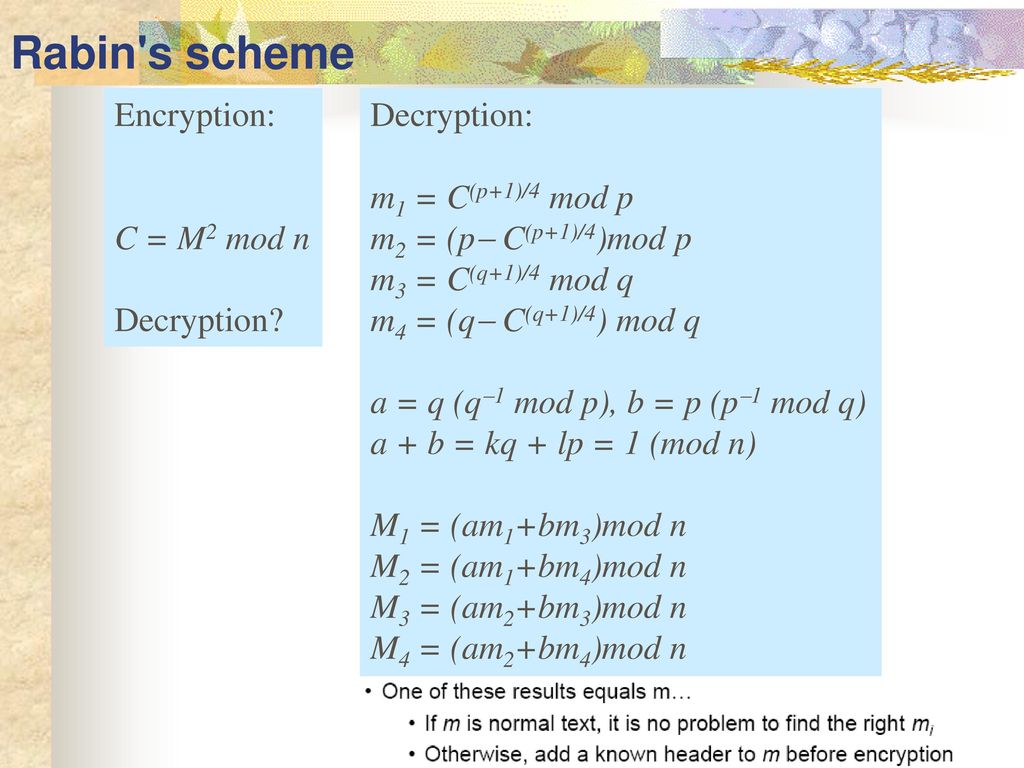



Applied Cryptography Spring 17 Asymmetric Ciphers Ppt Download
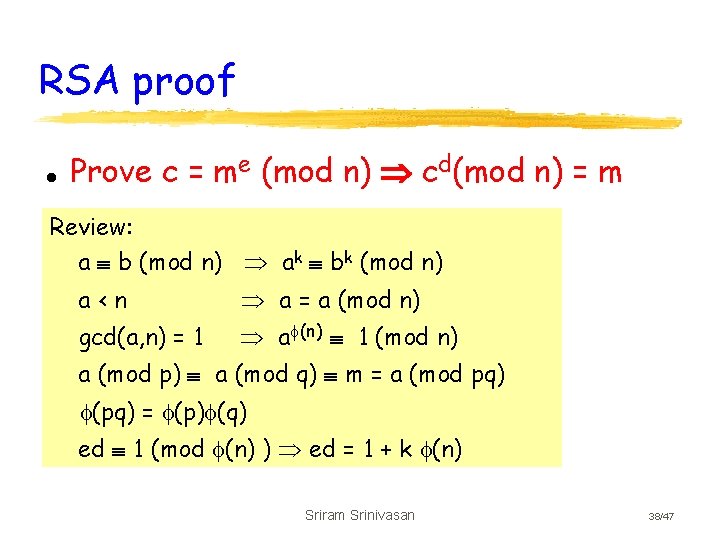



Inside Pk Cryptography Math And Implementation Sriram Srinivasan




Wangding Cup Crypto Shenyue2 Problem Solution Programmer Sought




Modulo Operation Wikipedia




22 C 19 Discrete Structures Integers And Modular




Pdf On The Constant In The Mertens Product For Arithmetic Progressions I Identities




An Attack Bound For Small Multiplicative Inverse Of F N Mod E With A Composed Prime Sum P Q Using Sublattice Based Techniques Semantic Scholar




Answered Theorem 1 Let C E N Be A Natural Bartleby
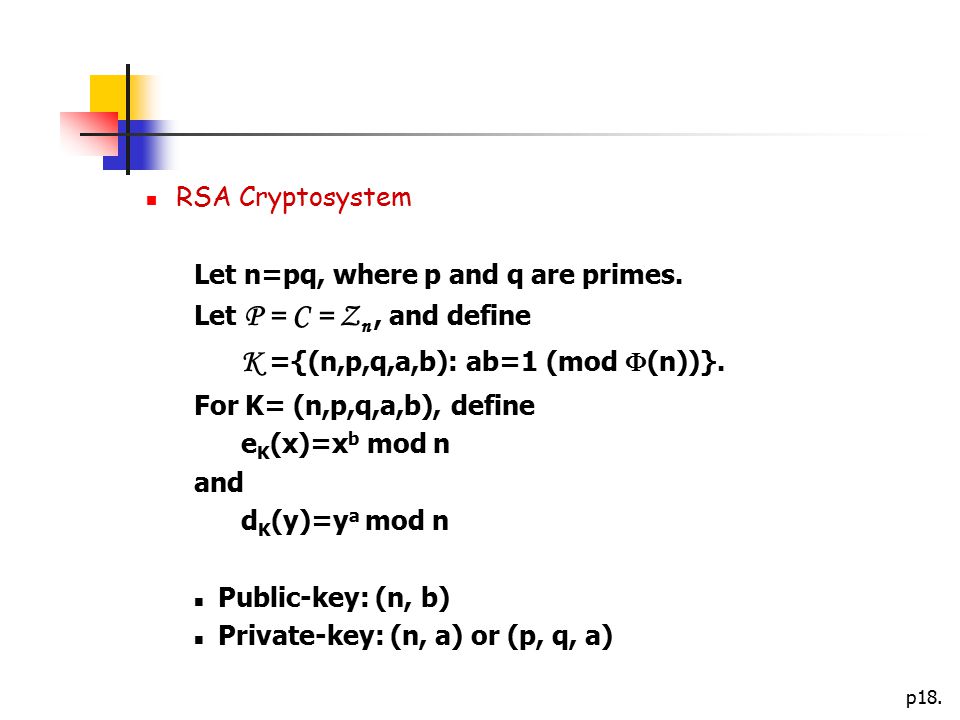



And Factoring Integers I Ppt Video Online Download




Ma2316 Introduction To Number Theory Tutorial 7 Question 1




Okamoto Uchiyama Crypto The Okamoto Uchiyama Technique Is A By Prof Bill Buchanan Obe Asecuritysite When Bob Met Alice Medium
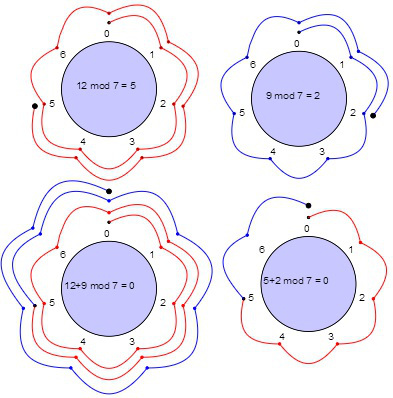



Modular Addition And Subtraction Article Khan Academy




Discrete Math Cs 2800 Prof Bart Selman Selmancs




Examples Of Sequences N Mod 1 With Q 256 A N 1 256 255 256 Download Scientific Diagram



Modular Arithmetic Wikipedia




Rsa Encryption Problem For Discrete Math Cryptography Stack Exchange



コメント
コメントを投稿